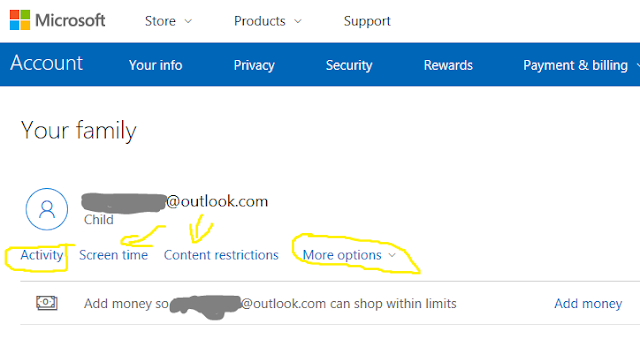
How to deal with cyber bullies.
So the SINGLE, MOST IMPORTANT THING YOU CAN DO, IS TO LOVE YOUR CHILD UNCONDITIONALLY. Tell them you love them, EVERY, SINGLE, DAY! Talk to them and make sure they know you trust them. Establish this trust EARLY. In case you aren't familiar with me, I have a degree in psychology, 20 years of cyber security experience, father of an autistic child and another on the way. Be aware of what they are and are not watching on TV, tablet, and telephone. Show them this! This video is POWERFUL. These same tactics work in real life and online. Show it to them several times. Will the tools in this video work every time? Probably not, but it will MOST of the time. The most powerful tool you can teach your children is KNOWLEDGE. Understanding. Most kids have been bullied, at some point in their lives. I was rarely a victim of bullying because I was the second tallest/biggest kid in my class up until about 8th grade. Eve...